This guide explains how to securely connect SYNQ to Redshift.We need this information so we collect metadata about your tables.To be able to finish this guide, you’ll need the following:
→ Access to modify your Redshift configuration⏱️ Estimated time to finish: 10 minutes.
→ Access to modify your Redshift configuration⏱️ Estimated time to finish: 10 minutes.
Data we collect
For the automated data anomaly testing we collect the following:- Number of rows in every table in the monitored dataset(s)
- Timestamp of the last change of data in all tables in the monitored dataset (see Freshness monitoring of tables for enabling this)
Step 4 goes through how to set permissions to allow access to querying raw data
Table Description svv_redshift_databases List of all the databases that a user has access to svv_all_schemas Summary of schemas svv_table_info Summary information for tables in the database svv_external_tables Details for external tables such as table and schema names
Setup Redshift access
Create a dedicated SYNQ user with sufficient permissions
-
Open the Query Editor in Redshift and make sure that we got the right cluster and database selected
-
Run the following SQL to create a SYNQ user and group with the sufficient permissions where
<password>is a secret you can set to be used by SYNQ -
Grant us permission to list tables and their columns in specific schemas. When used with views having
WITH NO SCHEMA BINDINGwe needUSAGEgrant for both schemas, the one in which late binding view is defined and the one from which it is reading. This has to be repeated for every schema:To grantUSAGEto all schemas one can use: - Grant access to tables within a schema (optional)
Whitelist the SYNQ app
For the complete list of SYNQ IP addresses by region, see SYNQ IP Whitelist.
-
From Redshift, navigate to
Workgroup configurationand click your default Workgroup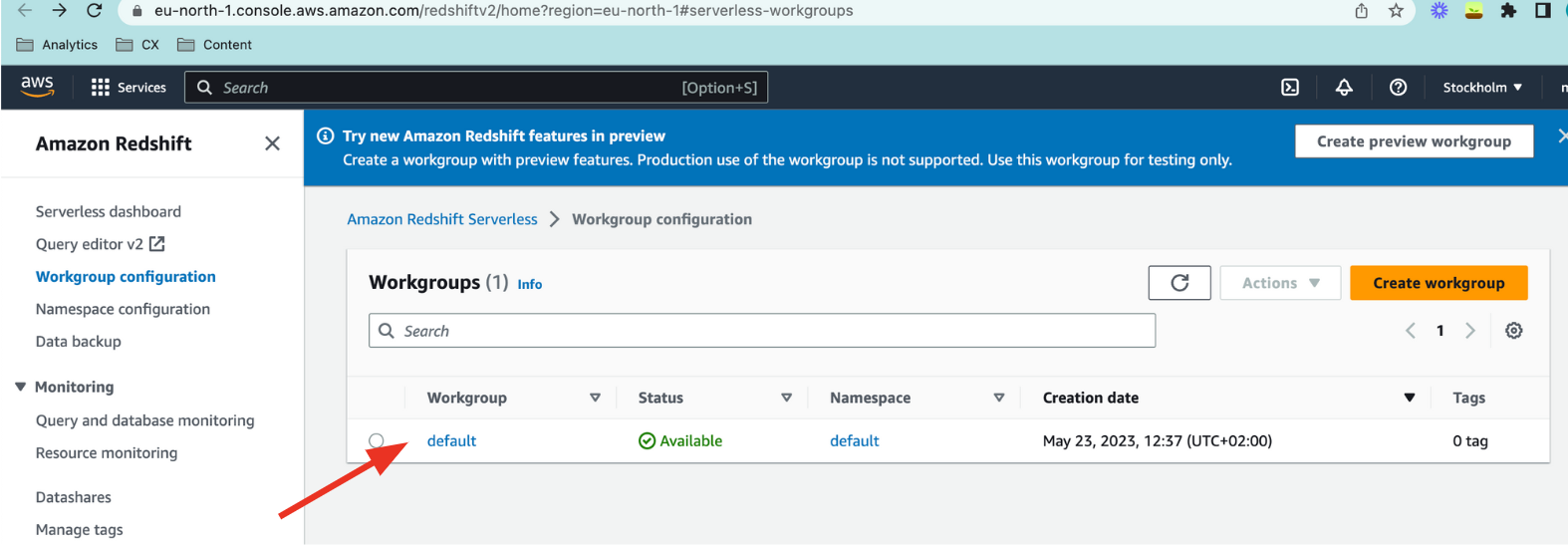
-
Under Network and security click
Editand check the Turn on Publicly accessible checkmark. Then clickSave changes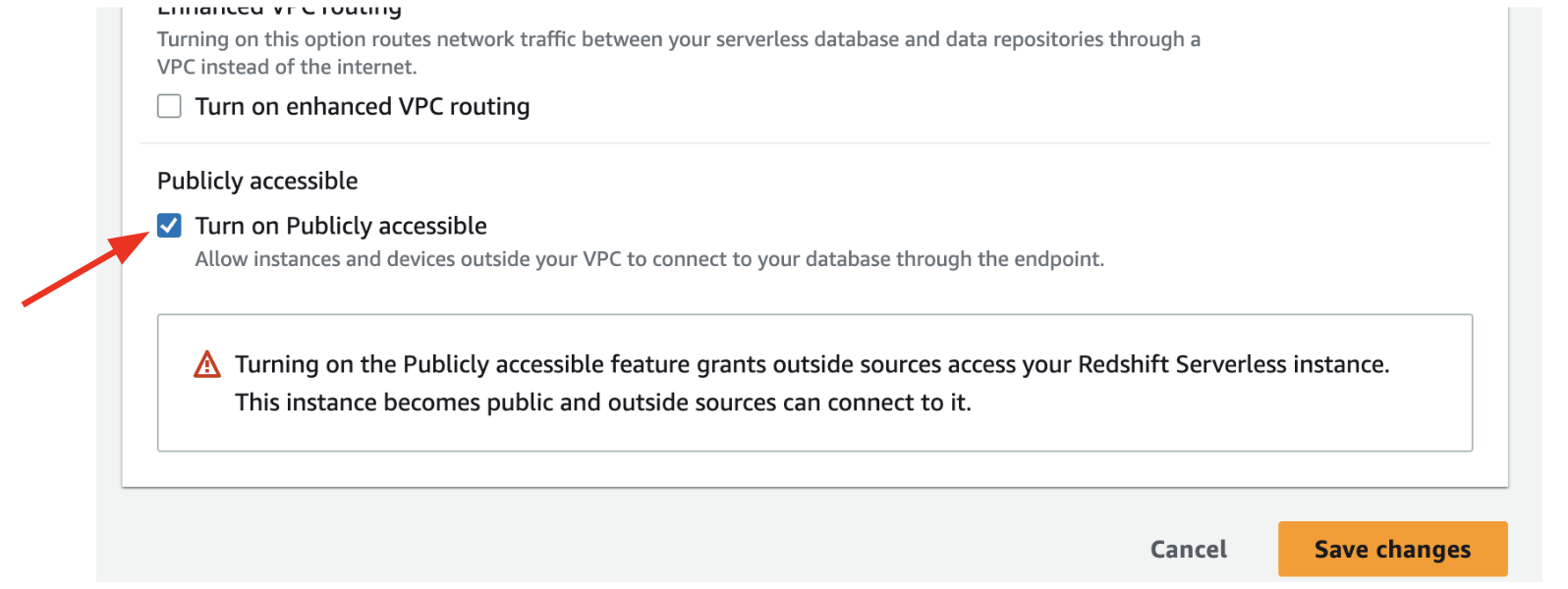
-
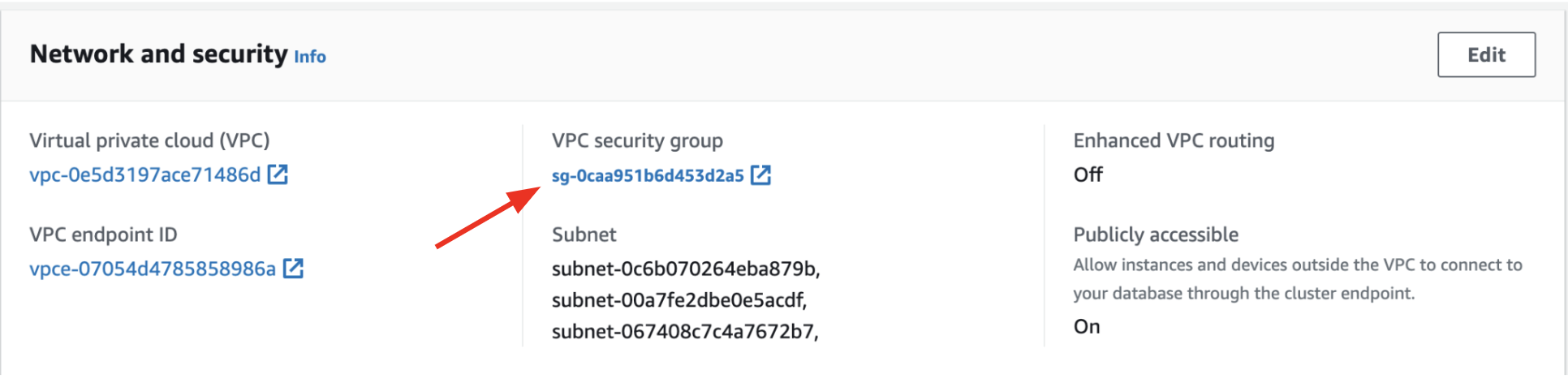
Close the window to return to the Workgroup space and click your VPC security group
-
Under the Inbound rules tab click
Edit inbound rules. Then clickAdd ruleand populate it with the following information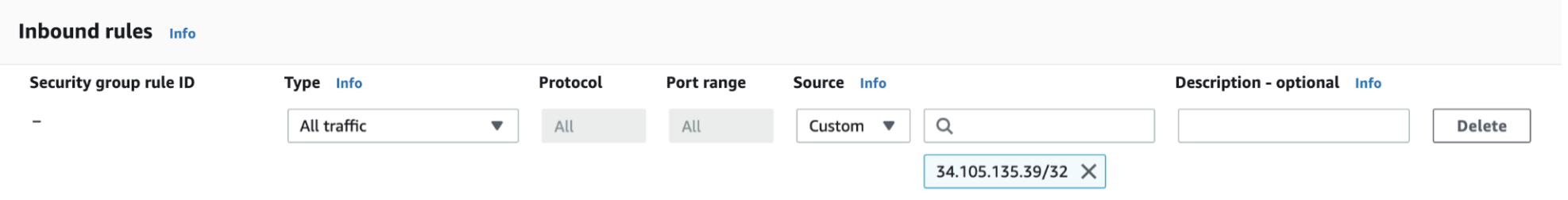
- Type:
All Traffic - Source:
Customwith the following value in the text field:34.105.135.39(EU) or35.238.250.82(US)
- Type:
-
Click
Save rules
Database, dataset and host name
-
Take a note of your database and dataset. These can be found in the Query Editor
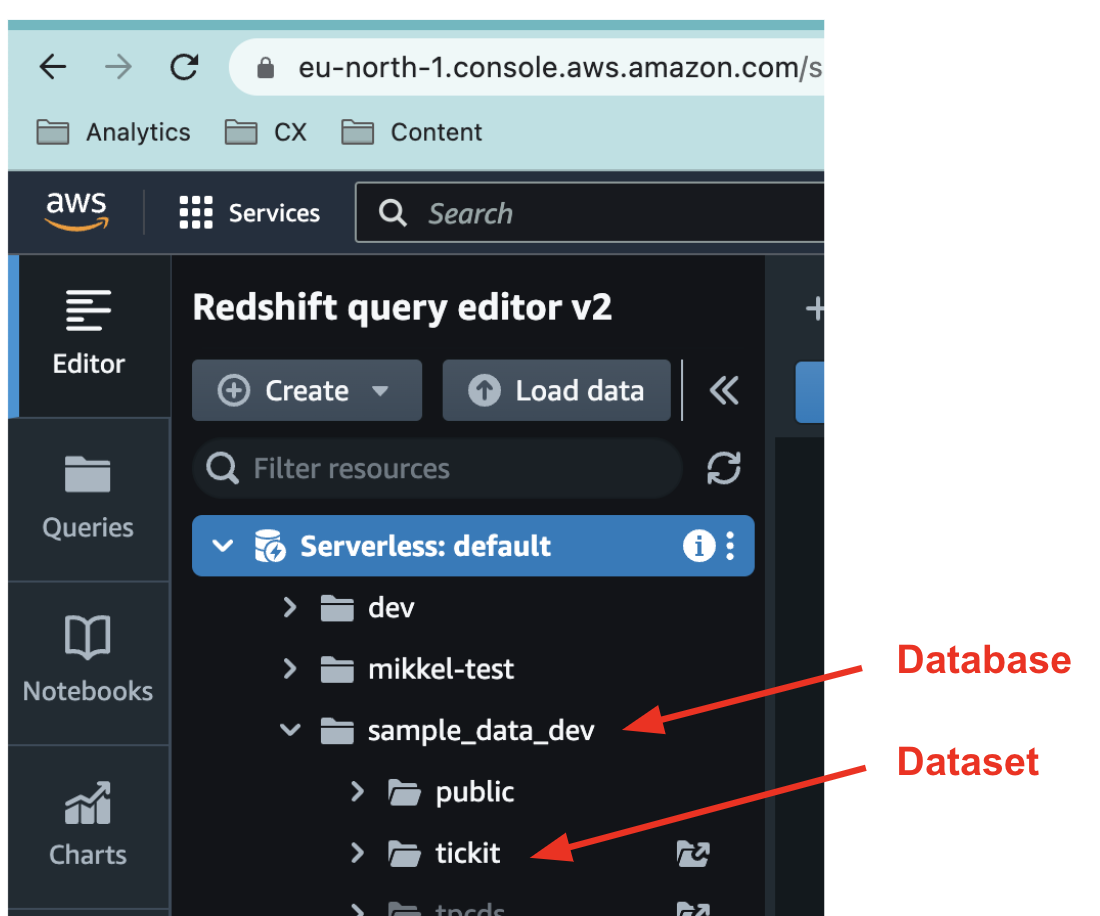
-
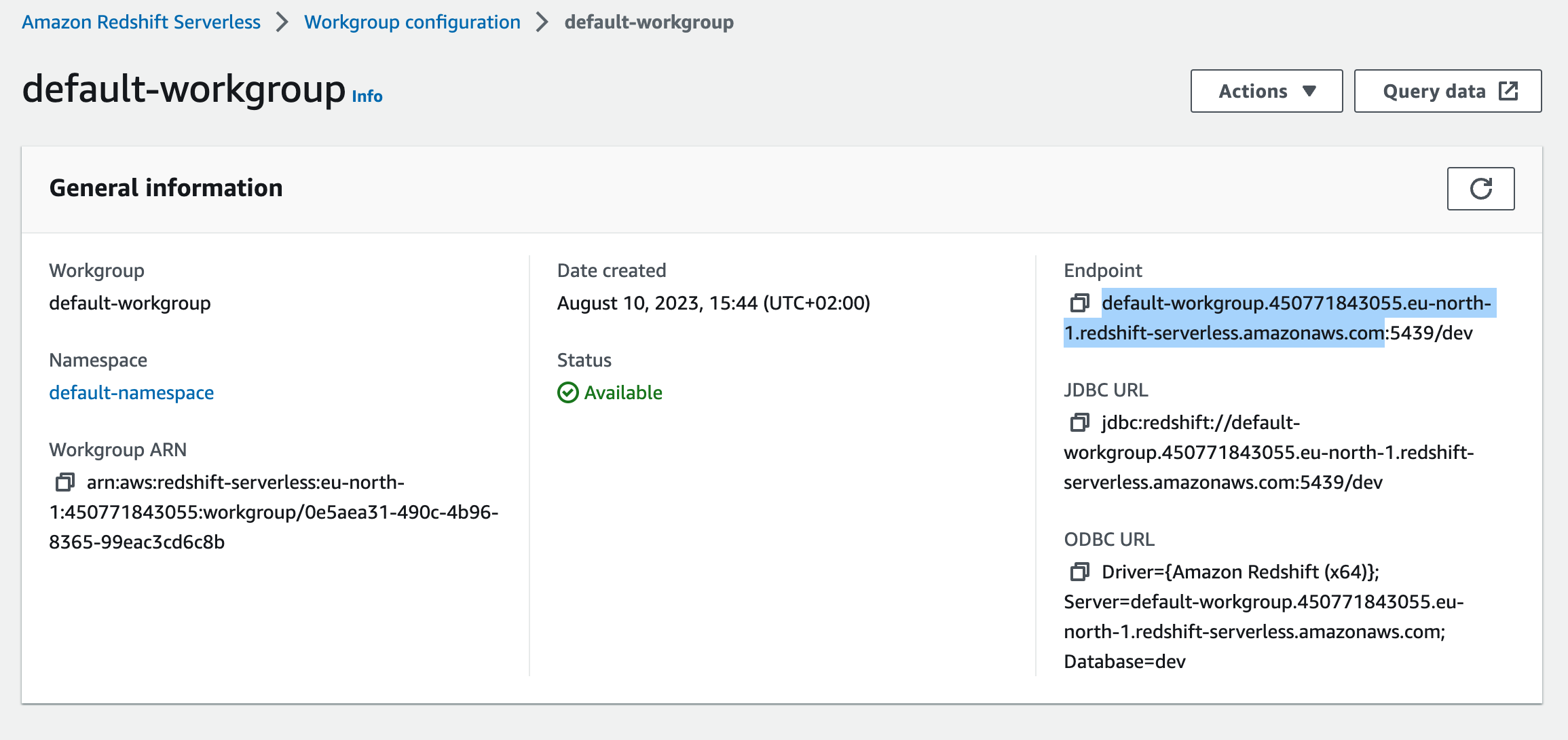
Go to
Workgroup configurationand select your default workgroup. Take a note of yourJDBC URL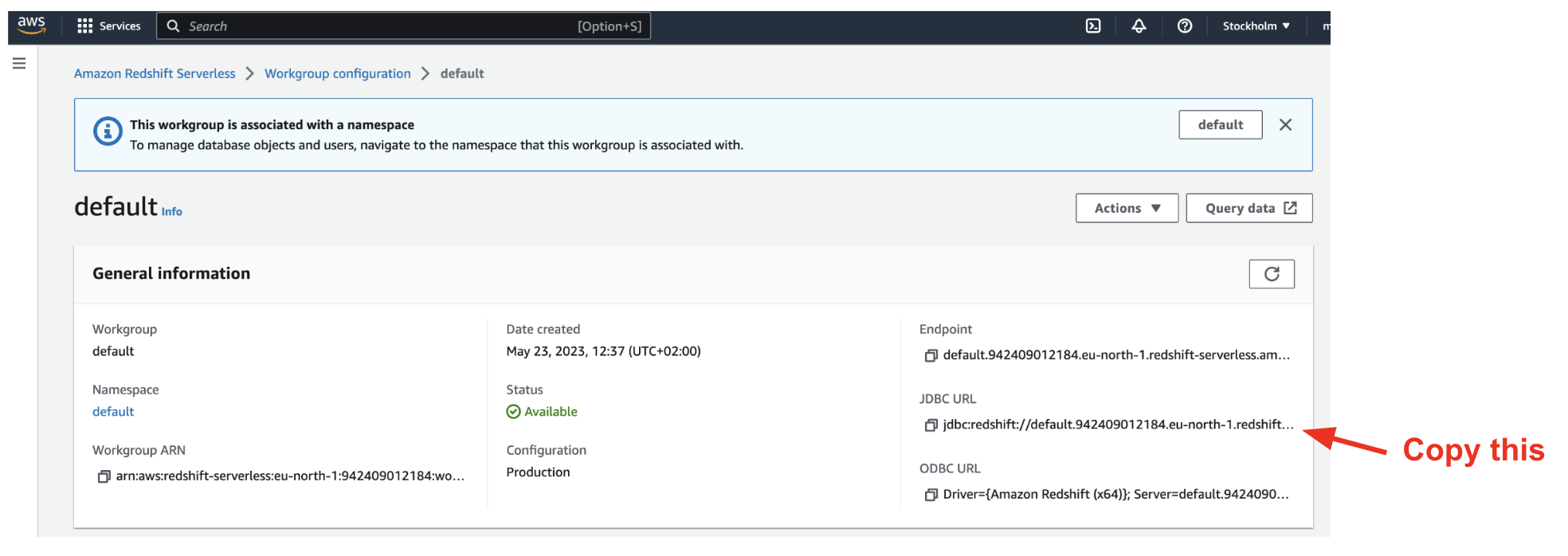
Input data in the SYNQ UI
Integration name
For exampleRedshift
Database
The name of your database (e.gexample_production_database)
Host
The name of your host (e.g.cluser-name.us-east-1.redshift.amazonaws.com)
To find the host, go to Workgroup configuration, and look at the Endpoint.
Copy everything until the amazonaws.com and leave out the rest. In most cases, that will be :5439/dev.
Paste it into the Host field in SYNQ.
Port
Port you specified earlier in the guide. Default port is5439
User and password
User and password you specified earlier in the guideDefault dataset
Dataset you want SYNQ to monitorIn some cases, permission groups can take a while to propagate.
If you keep getting a
Connect failed error after double-checking your details, try again later.